Overview for setting up trusted profiles
A trusted profile is a grouping of identities into a single, shared IAM identity. Create trusted profiles to quickly grant users, IAM access groups, compute resources, services, and service IDs access to your account without an invitation.
Through trusted profiles, enterprises can manage access and permissions to their IBM Cloud account from an on-premises IAM solution. This can be LDAP (Lightweight Directory Access Protocol) or some other user registry managed by your organization. Thanks to trusted profiles, enterprises avoid setting up IBM Cloud accounts for each user and are able to monitor, audit, and remove access by using their centralized IAM solution.
- Required roles
-
To configure identity providers for trusted profiles, you must have one of the following roles in the IBM Cloud account:
-
- Account owner
-
- Administrator role on all account management services
-
- Administrator role on the IAM Identity Service
Prerequisites:
To set up trusted profiles, you must first configure an App ID and an identity provider (for example, Azure Active Directory). For more information on configuring App ID to work with an identity provider, see Configuring App ID with your identity provider.
Setting up trusted profiles
To set up your trusted profile:
-
Log in to your IBM Cloud account and then navigate to Manage > Access(IAM) > Trusted profiles.
-
Click Create.
-
Type the name for the trusted profile and then click Continue.
-
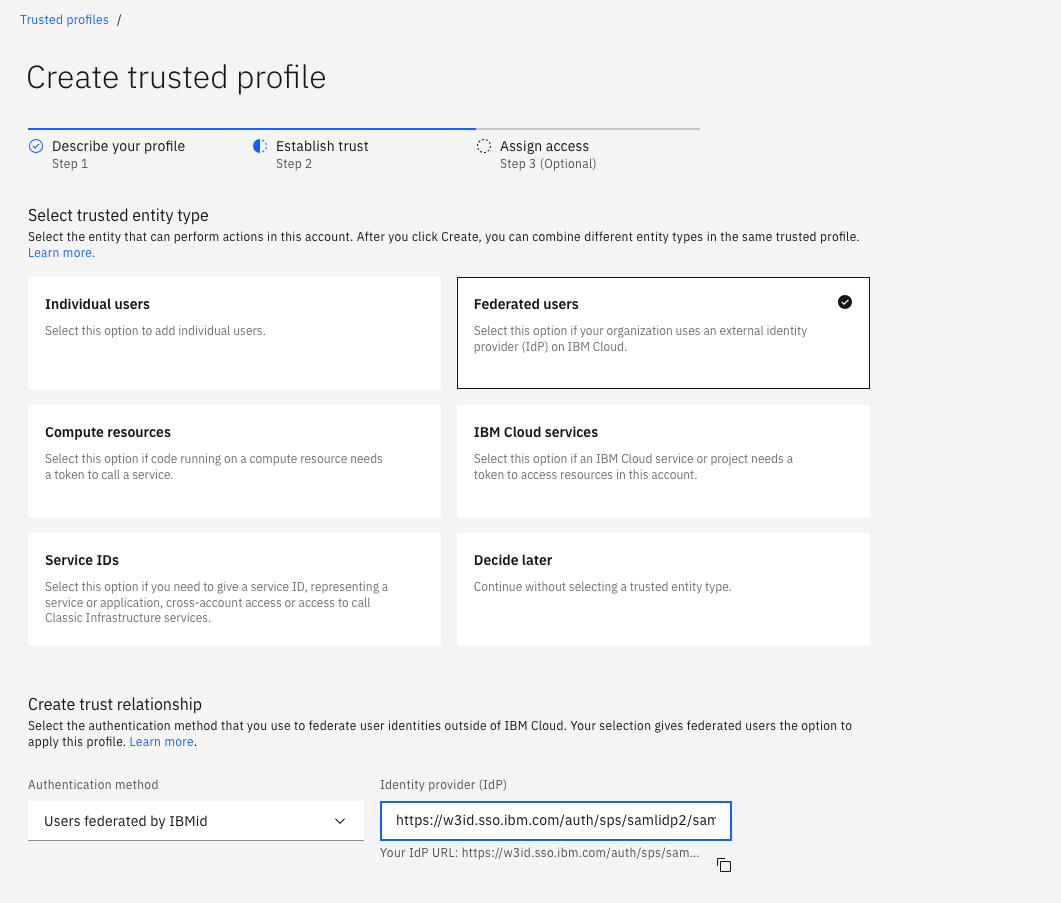
For trusted entity type, select Federated users.
-
For authentication method, select Users federated by IBM Cloud App ID.
-
In the Identity provider (IdP) text box, add the URL of your IdP's SAML endpoint.
-
Click Add a condition to start adding new access conditions.
-
From the Filter attributes pull-down menu, select an attribute that you want to use. For example:
email. To access details about the IdP's metadata schema, click the Expand icon next to Identity provider data. -
From the Qualifier pull-down menu, select one of the available conditions, for example, Equals
-
In the Value field, type the condition value, for example
[email protected]and then press Continue. -
For access type, select Access group or Access policy.
-
Create the policy: after each step, click Next.
- Select the service that the access policy applies to.
- Select the resources that the access policy applies to.
- Select the roles and actions that the access policy applies to.
-
Add any optional conditions, if applicable and then click Add. Your trusted profile is created.
Logging in with Trusted profiles
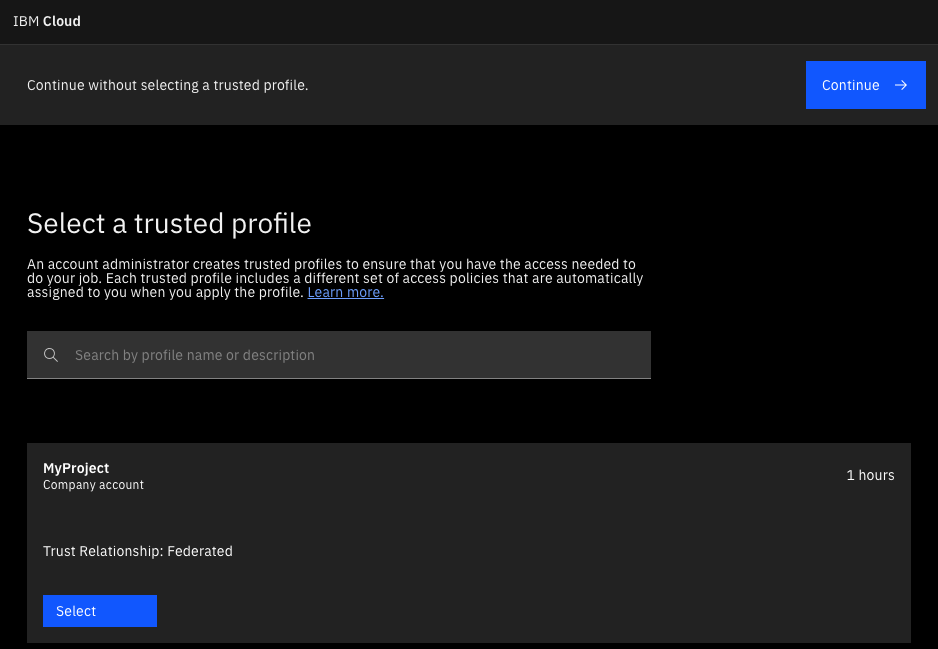
Users choose Trusted profiles as the login method on the Cloud Pak for Data as a Service login page. Then, they are redirected to their company's login page to enter their company credentials. Upon logging in successfully, they are redirected to the Cloud Pak for Data as a Service authentication page. On the authentication page they see a list of one or more trusted profiles that they were granted access to by an account administrator. They can select any of these profiles, depending on their specific use case.
Limitations
The following limitations apply:
If a user API key is required to authenticate runtime operations, this API key must be generated by one of the static users of trusted profiles. Static users are referred to as Individual users during the setup process and are added
to a trusted profile based on their IAM ID. If you're a federated user of trusted profiles (authenticated by an external identity provider), you must ask one of the static users to generate and share an API key for you. You won't be able to
generate an API key yourself. For more information on managing API keys, see Managing the user API key.
Learn more
Parent topic: Managing the platform